As cyberattacks grow increasingly sophisticated, the need for organizations to identify and mitigate risks to protect their valuable data and assets becomes ever more critical. While companies invest in capability building, new roles, external advisers, and control systems to counter cyber risk, many still lack an effective, integrated approach to cyber risk management and reporting.
This gap in understanding is highlighted in PwC’s 2022 Global Digital Trust Insights Survey, revealing that 60% of CEOs and other C-suite executives globally have less than a thorough understanding of the risk of data breaches, while 20% have little or no understanding at all of these risks. The question then arises: how can these leaders effectively steer their organizations toward cybersecurity resilience when the understanding of the risks is so limited?
Every organization faces cyber risk, which varies by industry, business size, regulatory environment, supply chain, and more. These risks necessitate a comprehensive approach to cybersecurity risk analysis. Such analysis is not just a tool for quantifying risks and assessing the effectiveness of security controls; it’s an essential practice for targeting your security budget and effective resource allocation.
But what makes a cybersecurity risk analysis truly insightful? For effective measurement and management of cybersecurity risks, incorporating a set of right cybersecurity metrics into the risk analysis framework is essential. These key performance indicators (KPIs) serve as a litmus test for an organization’s cybersecurity health, offering valuable insights and enabling progress tracking over time.
What are Cybersecurity Metrics and KPIs?
Cybersecurity metrics and Key Performance Indicators (KPIs) are essential tools that provide insights into the effectiveness of an organization’s cybersecurity strategy. They serve as quantifiable measurements that can help business leaders and security teams understand their cybersecurity posture, communicate effectively with stakeholders, and respond to risks cost-effectively and efficiently.
Cybersecurity metrics are tools used to assess and measure the performance and strength of an organization’s cybersecurity. They provide a measure of overall security health and can offer crucial data points to help strategize and prioritize areas where existing cyber procedures may be weak. These metrics provide quantitative information that can be used to show management and board members the seriousness with which you take the protection and integrity of sensitive information and IT assets.
On the other hand, KPIs in cybersecurity indicate progress toward defined security program goals. They revolve around strategic and general measures of success. By tracking KPIs and key risk indicators (KRIs), organizations can gain a clear understanding of how effective their cybersecurity efforts have been over time. This data can then inform future cybersecurity decisions.
Why is Cybersecurity Metrics Important?
Cybersecurity metrics play a crucial role in various aspects of an organization’s cybersecurity strategy, including:
- Compliance with Regulations: Cybersecurity metrics can help organizations demonstrate compliance with data privacy regulations such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA). These regulations have specific requirements for data security and incident reporting, and metrics can provide evidence that an organization is meeting these requirements.
- Meeting Industry Standards: Cybersecurity metrics can help organizations meet industry-specific security standards, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA). These standards often require organizations to track and report on specific cybersecurity metrics.
- Risk Assessment and Prioritization: Metrics provide a data-driven approach to risk assessment, enabling organizations to identify their most critical assets, prioritize vulnerabilities, and focus their security efforts accordingly.
- Measuring Progress and Effectiveness: Tracking metrics over time allows organizations to gauge the effectiveness of their cybersecurity initiatives, identify trends in cyberattacks, and evaluate the impact of security investments.
- Decision-Making and Resource Allocation: Metrics inform decision-making processes, helping organizations allocate resources effectively, prioritize security investments, and justify budget requests to management.
- Demonstrating Value and ROI: Metrics provide tangible evidence of the value of cybersecurity investments, allowing organizations to demonstrate their effectiveness in protecting sensitive data and assets.
- PII Protection Effectiveness: Metrics can provide tangible evidence of the effectiveness of Personally Identifiable Information (PII) protection measures, both to internal stakeholders and external regulators. This information can support compliance efforts, enhance stakeholder confidence, and improve an organization’s reputation for data stewardship.
- Benchmarking and Continuous Improvement: Metrics enable organizations to compare their security posture to industry benchmarks, identify areas for improvement, and continuously enhance their cybersecurity practices.
Key Metrics To Include in Your Cybersecurity Risk Analysis

1. Security Incidents
Security incidents offer a snapshot of how an organization’s security measures are performing over time. They help identify what’s working and what’s not, thereby informing decision-making about future projects. Moreover, they provide quantitative data that can be used to demonstrate to management and board members the seriousness with which the organization takes the protection and integrity of sensitive information and IT assets.
Security incidents can range from intrusion attempts to actual security breaches. This metric offers general insight into existing vulnerabilities, the state of preparedness, and how the organization responds to attacks.
Ask Yourself
- How many security incidents have we experienced in the past year? This will give you a baseline for comparison and help you track improvements over time.
- What types of security incidents are most common? Understanding the types of threats you face can guide your defense strategy.
- How quickly do we detect and respond to security incidents? Speed is critical in minimizing the impact of a security incident.
- What is the average cost of a security incident? This can include direct costs like recovery efforts and indirect costs like reputational damage.
- How effective are our existing security controls at preventing incidents? Regularly assessing the efficacy of your security controls can help you identify areas for improvement.
2. Intrusion Attempts
Intrusion attempts are another vital metric in cybersecurity risk analysis. They represent the number of times an unauthorized entity has tried to gain access to your system. Tracking intrusion attempts helps organizations identify patterns, understand the tactics and techniques used by attackers, and develop effective countermeasures. It also allows organizations to assess their detection capabilities and response times.
Moreover, comparing the number of intrusion attempts with actual security incidents can provide valuable insights into the state of an organization’s preparedness and how it responds to attacks.
Ask Yourself
- How many intrusion attempts have we experienced in the past year? This will help you understand the scale of the threat you face.
- What types of intrusion attempts are most common? This can guide your defense strategy and help you prioritize resources.
- How quickly do our intrusion detection systems detect threats? Early detection is crucial in preventing breaches.
- What proportion of intrusion attempts lead to actual security incidents? This can indicate the effectiveness of your security controls.
- How have the number and types of intrusion attempts changed over time? This can help you identify trends and adapt your security strategy accordingly.
3. Mean Time Between Failures (MTBF)
Mean Time Between Failures (MTBF) is a critical metric in cybersecurity risk analysis. It represents the average time that elapses from one unplanned breakdown to the next under normal operating conditions. The higher the MTBF, the more reliable the system. It indicates how long a system typically operates before failing.
Analyzing MTBF helps organizations understand how often a piece of equipment stops performing as expected, and so is an important measure of reliability. This information is crucial for prioritizing defense efforts and allocating resources effectively.
Moreover, tracking MTBF over time can help organizations identify trends, spot recurring issues, and measure the success of their cybersecurity programs.
Ask Yourself
- What is our system’s average MTBF? This will give you a baseline for comparison and help you track improvements over time.
- How does our MTBF compare to industry standards? Understanding where you stand compared to others can guide your improvement efforts.
- What factors contribute to our MTBF? Identifying these factors can help you address the root causes of failures.
- How does our MTBF affect our overall system reliability and availability? This can help you understand the impact of failures on your operations.
4. Mean Time to Detect (MTTD)
Mean Time to Detect (MTTD) is a key performance indicator in incident management. It refers to the average amount of time it takes for an organization to discover—or detect—an incident. The sooner an organization finds out about a problem, the better. For instance, in the software development field, we know that bugs are cheaper to fix the sooner you find them. When it comes to system outages, any second results in more financial loss, so you want to get your systems back online ASAP.
Tracking MTTD is crucial for several reasons. Firstly, it provides a measure of the threat landscape your organization faces. A high MTTD could indicate that your organization is slow at detecting incidents, which could lead to more severe consequences. Secondly, it can provide insights into the effectiveness of your incident detection mechanisms. If your MTTD is low, it could indicate that your detection mechanisms are effective.
Ask Yourself
- What is our system’s average MTTD? This will give you a baseline for comparison and help you track improvements over time.
- How does our MTTD compare to industry standards? Understanding where you stand compared to others can guide your improvement efforts.
- What factors contribute to our MTTD? Identifying these factors can help you address the root causes of failures.
- How does our MTTD affect our overall system reliability and availability? This can help you understand the impact of failures on your operations.
5. Mean Time to Recovery (MTTR)
Mean Time to Recovery (MTTR) is a key performance indicator that represents the average time required to restore a system to functionality after an incident. It includes the full time of the outage—from the time the system or product fails to the time that it becomes fully operational again.
Tracking MTTR is crucial as it tells how quickly you solve downtime incidents and get your systems back up and running. It’s a measure of the effectiveness of your incident response process. A high MTTR could indicate that your organization is slow at recovering from incidents, which could lead to more severe consequences. On the other hand, a low MTTR could indicate that your recovery
Ask Yourself
- What is our system’s average MTTR? This will give you a baseline for comparison and help you track improvements over time.
- How does our MTTR compare to industry standards? Understanding where you stand compared to others can guide your improvement efforts.
- What factors contribute to our MTTR? Identifying these factors can help you address the root causes of failures.
- How does our MTTR affect our overall system reliability and availability? This can help you understand the impact of failures on your operations.
6. Mean Time to Contain (MTTC)
Mean Time to Contain (MTTC) measures the average time it takes to detect, analyze, and contain a security incident. It encompasses the time required to detect and resolve incidents. At the same time, the IT team ensures that the probability of a similar incident is reduced. This makes MTTC an important measurement tool in the context of incident response management.
An enterprise is considered successful if its MTTC is 20 minutes or less. IBM’s “Cost of a Data Breach Report” states that the average MTTC for a breach is 280 days, which is much longer than an efficient 20 minutes.
Ask Yourself
- What is our historical MTTC, and how has it trended over time?
- How does our MTTC compare to industry benchmarks or averages?
- What factors have contributed to our MTTC in past incidents (e.g., type of attack, response time, etc.)?
- How might potential future cyber incidents impact our MTTC?
- What strategies can we implement to reduce our MTTC?
7. Cost per Incident
Understanding the cost per incident provides a tangible measure of the financial impact of a cyber incident, allowing organizations to allocate resources better and implement strategies to minimize potential losses.
The cost per incident in cybersecurity refers to the total expenses an organization incurs as a result of a cyber incident. This includes direct costs such as system repair and recovery, data recovery, and incident response efforts. It also encompasses indirect costs like reputational damage, loss of customer trust, legal fees, regulatory fines, and even the potential inability to attract new investors and creditors.
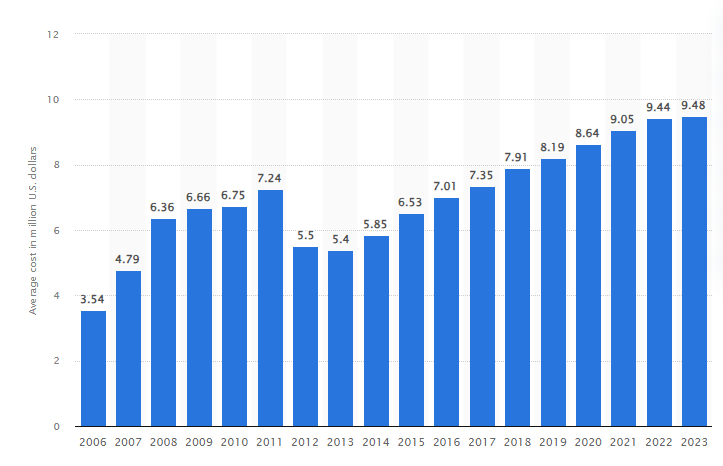
The cost of a data breach in the United States increased to an average of $9.48 million in 2023, compared to $9.44 million in the previous year. Globally, the average cost per data breach was $4.45 million in the same year.
Ask Yourself
- What is our historical cost per incident, and how has it trended over time?
- How do our costs per incident compare to industry benchmarks or averages?
- What factors have contributed to the cost of past incidents (e.g., type of attack, response time, etc.)?
- How might potential future cyber incidents impact our cost per incident?
- What strategies can we implement to reduce our cost per incident?
8. Security Awareness Training
Cybersecurity awareness training involves educating employees about the various security threats they could face and the best practices to mitigate these threats. The training covers a wide range of topics, including how to identify phishing attempts, the importance of strong passwords, and the proper handling of sensitive data.
Tracking the progress and effectiveness of Cybersecurity Awareness Training is important for several reasons. Firstly, it provides a measure of the cybersecurity knowledge within your organization. A well-educated workforce is your first line of defense against cyber threats. Secondly, it can provide insights into the areas where further training may be needed.
Ask Yourself
- What is the frequency of our cybersecurity awareness training?
- How engaged are our employees in the training?
- What is the completion rate of our training modules?
- How are we measuring human risk in our organization?
- How are we tracking the progress of our cybersecurity awareness campaign?
- Are there specific topics or questions that employees struggle with during the training?
- How are we measuring the performance of certain departments and individuals that fall into more high-risk roles?
9. Vendor Patching Cadence
Vendor patching cadence measures how often an organization reviews systems, networks, and applications for updates that remediate security vulnerabilities. This metric provides a comprehensive view of an organization’s ability to maintain up-to-date systems and protect against known vulnerabilities.
Vendor patching cadence refers to the frequency at which software vendors release updates or patches to fix security vulnerabilities in their products. A robust patching cadence is essential to ensure that all digital assets, including servers, routers, and applications, are protected against known vulnerabilities.
Ask Yourself
- How often do our vendors release security patches?
- How quickly are we able to apply these patches across our systems?
- What is our process for tracking and applying patches?
- How do we prioritize patches for critical vulnerabilities?
- What is our strategy for managing patches across multiple vendors?
10. Mean Time For Vendor Incident Response (MTVIR)
Mean Time For Vendor Incident Response measures the average time it takes for a vendor to control, remediate, and eradicate a threat after it has been identified. This metric provides insight into how quickly your vendor’s incident response team can help you and impacted systems return to normalcy.
The efficiency of your vendors’ incident response is crucial for minimizing the risk of data breaches. The longer it takes vendors to respond to incidents, the higher the chance you will suffer from a third-party data breach. MTVIR can also serve as evidence to demonstrate adherence to security policies. For example, metrics like MTVIR are often required for standards that necessitate proactive redressal of incidents.
Ask Yourself
- What is our historical MTFVIR, and how has it trended over time?
- How does our MTFVIR compare to industry benchmarks or averages?
- What factors have contributed to our MTFVIR in past incidents (e.g., type of attack, response time, etc.)?
- How might potential future cyber incidents impact our MTFVIR?
- What strategies can we implement to reduce our MTFVIR?
11. Security Ratings
Security ratings, also known as cybersecurity ratings, are data-driven, objective, and dynamic measurements of an organization’s security performance. They provide a comprehensive view of the overall cybersecurity posture. These ratings gather data from public and private sources via non-intrusive means, analyze the data, and rate security using proprietary scoring methodologies.
Security ratings differ among various vendors. Some may measure a single point in time or an organization’s exposure at the moment. Others assign a rating based on an organization’s ongoing program performance over time.
Ask Yourself
- What is our current security rating, and how has it trended over time?
- How does our security rating compare to industry benchmarks or averages?
- What factors have contributed to our security rating (e.g., type of attack, response time, etc.)?
- How might potential future cyber incidents impact our security rating?
- What strategies can we implement to improve our security rating?
12. Access management
Access management, also known as identity and access management (IAM), involves ensuring that the right individuals have access to the right resources at the right times for the right reasons. It encompasses user provisioning, password management, and access governance. Effective access management can help prevent unauthorized access to systems and data, thereby reducing the risk of data breaches.
Ask Yourself
- How are we managing access to our systems and data?
- How often do we review and update access privileges?
- How quickly can we revoke access when necessary?
- How are we ensuring that access privileges are granted based on the principle of least privilege?
- What strategies can we implement to improve our access management?
13. Security policy compliance
Security policy compliance refers to the degree to which an organization’s practices align with its established security policies. These policies typically cover areas such as access management, data protection, network security, and incident response.
Effective security policy compliance can help prevent unauthorized access to systems and data, thereby reducing the risk of data breaches. It can also help organizations meet regulatory requirements.
Ask Yourself
- How are we ensuring compliance with our security policies?
- How often do we review and update our security policies?
- How quickly can we adapt our practices when our security policies change?
- How are we ensuring that our security policies align with the latest regulatory requirements?
- What strategies can we implement to improve our security policy compliance?
14. Non-human traffic (NHT)
Non-human traffic refers to any online activity that isn’t generated or done by humans. It is generally generated by bots, which are programs created to visit websites for various reasons. From advanced bots, botnets, and web crawlers, among others, NHT can be a significant concern for businesses online because it is becoming so widespread. In fact, bot traffic now makes up nearly half of all internet traffic.
NHT can result in inflated traffic, decreased profits, and page optimizations that could lead to a drastically negative impact on your online presence. Fraudulent traffic can also be a precursor to cyberattacks and can be used to steal tickets, attempt phishing, send spam and malware, and conduct credential stuffing and denial of service attacks.
Ask Yourself
- What percentage of our network or website traffic is non-human?
- How are we identifying and categorizing non-human traffic?
- What measures are we taking to mitigate the impact of non-human traffic?
- How are we ensuring that our traffic data is not skewed by non-human traffic?
- What strategies can we implement to improve our handling of non-human traffic?
Bottom Line
The significance of cybersecurity risk analysis is undeniable. Cybersecurity metrics are not just numbers but a narrative of your organization’s resilience against cyber threats. They are the compass that guides your cybersecurity journey, ensuring you’re not just reacting but proactively strategizing. Remember, in cybersecurity, the goal isn’t to reach a destination but to keep moving forward. Stay vigilant, stay measured, and above all, stay secure!



14 Key Metrics to Include in Your Cybersecurity Risk Analysis