Code injection attacks are no longer confined to large corporations. According to a study on cybercrime conducted by Accenture, it has been found that small businesses are the target of approximately 43% of all cyber-attacks. This is one of the most common and dangerous types of cyberattacks that can compromise the security and functionality of web applications. It occurs when an attacker inserts malicious code into a web application, which is then executed by the server or the browser. The malicious code can have various harmful effects, such as stealing sensitive data, defacing web pages, taking over accounts, or executing remote commands.
According to Statista, SQL Injection, Stored Cross Site Scripting, and Command Injection were the most common code injection vulnerabilities in 2022, accounting for 33%, 26.7%, and 10.8% of all web application attacks, respectively.
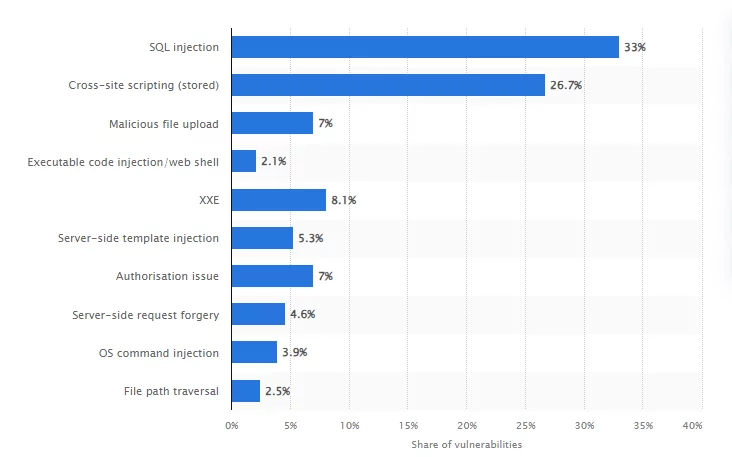
Moreover, code injection vulnerabilities are often ranked among the top security risks by organizations such as OWASP and SANS. Therefore, web developers and security professionals need to understand what code injection is, how it works, and how to prevent it.
In this article, we will guide you on how to prevent code injection attacks.
What is Code Injection?
Code injection vulnerabilities enable attackers to insert harmful code into a source code. The application then interprets and executes the malicious code. Attackers exploit these vulnerabilities by creating a code segment using external data without adequate input validation. The malicious code is usually designed to manipulate data flow, which leads to loss of confidentiality and reduced application availability.
Attackers can develop malicious code by exploiting user input validation flaws, such as data format, allowed characters, and expected data amount. Code injection vulnerabilities are rather rare, but when they do pop up, it is often a case where the developer has attempted to generate code dynamically.
How Code Injection Works
Code Injection, also referred to as Remote Code Execution or Code Evaluation, involves the unauthorized alteration of an executable or script that contains malicious code. Cybercriminals commonly survey the application for vulnerable points that can accept untrusted data and utilize it to execute program code. Such vulnerabilities may encompass various forms of input, including file uploads, form fields, cookies, and query string parameters.
The introduction of code is often achieved by directly concatenating character strings or using the PHP eval() function or its equivalent in another language. By inserting code as user input, the attacker abuses the program. The attackers gain access to the system information and database after the attack is successful.
What are Common Types of Code Injection Attacks?
Code injection attacks vary based on the application’s source code language and the attacker’s code. Below are common injection attack categories:
- XSS Attack: Cross-site scripting (XSS) is a type of code injection attack that allows an attacker to inject malicious client-side scripts into a web page, which are then executed by the browser of a victim who visits the page.
- LDAP Injection: Lightweight Directory Access Protocol (LDAP) injection is a type of code injection attack that exploits a web application that uses LDAP services to access data stored in a directory server. An attacker can inject malicious LDAP statements into a user input field, which are then executed by the server.
- SQL Injection: Structured Query Language (SQL) injection is a type of code injection attack that exploits a web application that uses SQL queries to interact with a database. An attacker can inject malicious SQL statements into a user input field, which are then executed by the database server.
- Command Injection: Command injection is a type of code injection attack that exploits a web application that executes system commands on the server. An attacker can inject malicious commands into a user input field, which are then executed by the operating system shell.
- XPath Injection: XPath Injection attacks occur when a website uses user-supplied information to construct an XPath query for XML data. By sending intentionally malformed information into the web application, an attacker can gain access to data that they normally would not be able to retrieve.
- HTML Injection: This type of attack is similar to XSS, but it involves injecting HTML code into a vulnerable website. The injected HTML code can be used for various purposes, such as defacing websites or redirecting users to other sites.
To read more about these and other types of code injection attacks, check out our detailed blog post: 10 Types of Malware Injection Attacks.
Common Code Injection Vulnerabilities
Code injection vulnerabilities often arise from a few common issues in how user input is handled and processed. Here are some areas where code injection vulnerabilities commonly occur due to specific actions or inactions by users and developers:
- Unvalidated User Input: If user input is not validated, sanitized, or escaped before being processed by the application, it can lead to various types of code injection attacks. This is because an attacker can insert malicious code into the input fields, which the application then executes.
- Insecure Direct Object References (IDOR): If an application exposes internal implementation objects (like files, database records, or keys) to users without access controls, it can lead to code injection attacks. An attacker can manipulate these references to gain unauthorized access to data.
- Insecure Use of Interpreters: If an application uses an interpreter in an insecure manner, such as using the eval() function in JavaScript or PHP without proper sanitization of user input, it can lead to code injection attacks.
- Insecure Data Deserialization: When applications deserialize data from untrusted sources without proper validation and sanitization, it can lead to code injection attacks. An attacker can manipulate the serialized data to inject malicious objects or code.
- Misconfigured Web Servers: If a web server is misconfigured, it can lead to code injection attacks. For example, if the server is configured to execute files with certain extensions (like .php or .js), an attacker could upload a file with that extension containing malicious code.
- Insecure Dependency Management: If an application uses outdated libraries or frameworks that contain known vulnerabilities, it can lead to code injection attacks. An attacker could exploit these vulnerabilities to inject malicious code.
- Lack of Proper Error Handling: If an application does not properly handle errors, it can reveal sensitive information that could be used in a code injection attack. For example, detailed error messages could reveal the structure of the application’s database or the internal workings of the application.
- Inadequate Security Configurations: Weak security configurations like weak passwords, default configurations, unnecessary services running, etc., can lead to code injection attacks.
How to Identify A Code Injection Vulnerability

Here are some steps and tools that can help you identify these vulnerabilities:
1. Review Code
A manual review of the source code is one of the most straightforward methods to identify potential code injection vulnerabilities. Developers should look for instances where user input is directly used in code execution without proper validation or sanitization. For example, if an application passes a parameter sent via a GET request to the PHP include() function with no input validation, this could potentially lead to a code injection vulnerability.
2. Use Analysis Tools
There are a number of different tools that can be used to detect injection attacks. These tools can be divided into three main categories:
- Static application security testing (SAST) tools: SAST tools scan the source code of a web application for potential vulnerabilities, including code injection vulnerabilities.
- Dynamic application security testing (DAST) tools: DAST tools scan a running web application for vulnerabilities, including code injection vulnerabilities.
- Interactive application security testing (IAST) tools: IAST tools combine SAST and DAST techniques to provide a more comprehensive analysis of a web application for vulnerabilities.
SAST tools
SAST tools are typically used by developers during the development process to identify and fix code injection vulnerabilities. These tools can be integrated into your Integrated Development Environment (IDE) and can help detect issues during software development. SAST tools can also be used by security teams to audit the security of a web application before it is deployed.
Some common SAST tools include:
DAST tools
DAST tools are typically used by security teams to test the security of a web application after it is deployed. DAST tools can be used to identify code injection vulnerabilities that may have been missed by SAST tools or that were introduced after the web application was deployed.
Some common DAST tools include:
IAST tools
IAST tools are a newer type of application security testing tool that combines SAST and DAST techniques to provide a more comprehensive analysis of a web application for vulnerabilities. IAST tools are typically used by security teams to test the security of complex web applications.
Some common IAST tools include:
3. Fuzz Testing
Fuzz testing, also known as fuzzing, involves intentionally sending malformed or unexpected data to an application’s inputs. By monitoring the application’s response, potential vulnerabilities can be identified and addressed.
4. Penetration Testing
Penetration testing involves simulating a real-world attack on your application to identify vulnerabilities. A penetration tester will use various methods, including code injection, to try and exploit potential security weaknesses.
Remember, no single method or tool can guarantee complete coverage of all potential code injection vulnerabilities. Therefore, it’s recommended to use a combination of these methods and tools for a more comprehensive vulnerability detection.
Best Practices to Prevent Code Injection Attacks

Validate User Input and Sanitize User Input
Input validation is a crucial process that involves verifying whether the user input satisfies certain predefined criteria, such as accurate format, length, or type, before it is processed or stored. The primary objective of input validation is to guarantee that the data remains safe and relevant for its intended usage. Below are some of the commonly used examples of input validation:
- Username Validation: Usernames should only contain alphanumeric characters (letters and numbers) and be at least 3 characters long. Use a regular expression to check if the username meets the criteria: /^[a-zA-Z0-9]{3,}$/.
- Password Validation: Passwords should be at least 8 characters long. Check if the length of the password is at least 8 characters.
- Email Validation: Email addresses should be in a valid format (e.g., user@example.com). Use a regular expression to verify the email format: /^[^\s@]+@[^\s@]+\.[^\s@]+$/.
- Numeric Input Validation: Input should be a positive integer. Check if the input is a number and if it is greater than 0.
Input sanitization removes harmful characters and scripts from user input to prevent security vulnerabilities, like cross-site scripting attacks. Examples of input sanitization include…
- HTML Tag Sanitization: Use a library like Validator.js to remove HTML tags from user input to prevent XSS attacks. Example: validator.stripTags(input).
- Escape Special Characters: Escape special characters, such as <, >, and &, to prevent HTML injection attacks. Example:
validator.escape(input). - Preventing SQL Injection: Use parameterized queries or prepared statements when interacting with databases to prevent SQL injection attacks. This involves using placeholders for user input in SQL queries.
Use Allowlists
One of the best practices for preventing code injection attacks is to use allowlists, also known as whitelists, to define acceptable input values. An allowlist is a list of characters, words, or patterns that are allowed in user input while everything else is rejected or filtered out. By using allowlists, we can ensure that only safe and expected input is processed by the application and avoid the risk of executing malicious code injected by attackers.
Some examples of using allowlists are:
- Regular expressions: Use regular expressions to match user input against a predefined pattern that specifies the allowed characters, length, and format. For example, to validate an email address, we can use the following regular expression: /^[^\s@]+@[^\s@]+\.[^\s@]+$/.
- Input validation libraries: Use input validation libraries, such as Validator.js for JavaScript or OWASP Java Encoder for Java, to validate and sanitize user input based on predefined rules and allowlists. For example, to remove HTML tags from user input, we can use the validator.stripTags(input) function from Validator.js.
- Parameterized queries: Use parameterized queries or prepared statements when interacting with databases to prevent SQL injection attacks. This involves using placeholders for user input in SQL queries, which are then replaced by the actual values after validating them against an allowlist. For example, to execute a query that selects a user based on their username and password, we can use the following parameterized query in Java:
PreparedStatement stmt = conn.prepareStatement(\"SELECT * FROM users WHERE username = ? AND password = ?\"); stmt.setString(1, username); stmt.setString(2, password); ResultSet rs = stmt.executeQuery();.
Avoid Client-Side Validation
Client-side validation is a common practice in web development that involves checking user input on the client’s browser before it is sent to the server. While client-side validation can improve user experience by providing immediate feedback, it should not be relied upon for security purposes.
The reason for this is simple: the client-side environment is under the control of the user, and therefore it can be manipulated. For example, an attacker can easily bypass client-side validation by altering JavaScript code loaded in the browser or making a basic HTTP call to the backend with a parameter that causes a code injection. This means that even if your application has robust client-side validation mechanisms, they can be rendered ineffective by a determined attacker.
Secure Coding Practices
Minimal Access Privileges
Minimal access privileges, also known as the “principle of least privilege,” is a security principle that restricts users and components to the minimum level of access required to perform their tasks. This practice limits the potential damage caused by code injection attacks by reducing the attack surface.
Example: In a web application, you may have different user roles, such as administrators, moderators, and regular users. The principle of least privilege ensures that each role has only the necessary permissions. For example, an administrator can perform actions like user management, while a regular user can only update their profile. This restricts the impact of a potential code injection attack, as an attacker with limited access cannot manipulate critical functionality.
Secure Password Hashing Algorithms
Secure password hashing involves transforming user passwords into a format that cannot be easily reversed. It’s crucial for safeguarding user credentials against theft and ensuring the confidentiality of sensitive data.
Example: Instead of storing passwords in plaintext, a secure password hashing algorithm like bcrypt is used. When a user registers, their password is hashed and stored. During login, the system hashes the entered password and compares it to the stored hash. For instance:
# Python example using bcrypt
import bcrypt
password = "my_secure_password".encode('utf-8')
salt = bcrypt.gensalt()
hashed_password = bcrypt.hashpw(password, salt)
# Store 'hashed_password' and 'salt' in the databaseParameterized SQL Queries
Parameterized SQL queries separate user input from SQL query logic, preventing SQL injection attacks. Instead of directly including user input in SQL queries, placeholders are used to bind user inputs securely.
Example: In PHP, you might use prepared statements to create parameterized SQL queries:
// Establish a database connection
$pdo = new PDO("mysql:host=localhost;dbname=mydb", "username", "password");
// User input
$user_id = $_POST['user_id'];
// Create a parameterized query
$stmt = $pdo->prepare("SELECT * FROM users WHERE id = :user_id");
$stmt->bindParam(':user_id', $user_id, PDO::PARAM_INT);
$stmt->execute();Cryptography for Sensitive Data
Cryptography involves the transformation of sensitive data into an unreadable format using encryption. This is essential to protect data even if an attacker gains access to the storage.
Example: Encrypting sensitive data, such as credit card numbers, before storing them in a database:
import javax.crypto.Cipher;
import javax.crypto.KeyGenerator;
import javax.crypto.SecretKey;
// Generate a secret key
KeyGenerator keyGen = KeyGenerator.getInstance("AES");
keyGen.init(256);
SecretKey secretKey = keyGen.generateKey();
// Encrypt sensitive data
Cipher cipher = Cipher.getInstance("AES");
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
byte[] encryptedData = cipher.doFinal(sensitiveData);HTTPS for Data in Transit
HTTPS encrypts data during transmission, preventing eavesdropping and ensuring data integrity. This is crucial for protecting sensitive information while it travels between clients and servers.
Example: Configuring HTTPS in an Apache web server:
- Acquire an SSL/TLS certificate from a trusted Certificate Authority (CA).
- Install and configure the certificate in your web server’s configuration files.
- Ensure that the server enforces HTTPS by redirecting HTTP traffic to the secure HTTPS connection.
Avoid Hardcoding Secrets in Code
Hardcoding secrets like API keys or passwords directly into your code can lead to security vulnerabilities. It’s essential to store secrets securely using environment variables or dedicated secret management solutions.
Example: Storing an API key as an environment variable in a Python application:
import os
api_key = os.environ.get("API_KEY")
# Use 'api_key' in your code without revealing the actual keyKeep Code Up-to-Date
Keeping your codebase up-to-date with the latest security patches and updates is crucial to prevent code injection attacks. Outdated software often contains known vulnerabilities that attackers can exploit.
Implement a regular update and patch management process that involves:
- Monitoring security advisories for all components and dependencies.
- Testing updates in a controlled environment to ensure they do not introduce new issues.
- Scheduling and conducting routine updates to mitigate potential vulnerabilities.
JavaScript-Specific Measures
Avoid eval(), setTimeout(), and setInterval()
The use of eval(), setTimeout(), and setInterval() can introduce security vulnerabilities in your JavaScript code. Avoid them whenever possible to reduce the risk of code injection.
Example:
Avoiding eval(): Instead of using eval() to execute dynamic code, use function calls or conditional statements:
// Avoid using eval()
const code = "alert('Hello, World!');";
eval(code);
// Use a function or a conditional statement
function showAlert() {
alert('Hello, World!');
}
showAlert();Avoiding setTimeout() and setInterval():
Be cautious when using these functions with dynamic code. Instead, pass a function reference:
// Avoid using setTimeout() with dynamic code
const code = "alert('Hello, World!');";
setTimeout(code, 1000);
// Pass a function reference
function showAlert() {
alert('Hello, World!');
}
setTimeout(showAlert, 1000);Avoid new Function()
The new Function() constructor creates a new function with the specified arguments, which can lead to security risks if used improperly. Avoid this constructor to prevent dynamic code execution.
Example:
Avoiding new Function(): Use named functions or anonymous functions when needed instead of new Function():
// Avoid using new Function()
const add = new Function('a', 'b', 'return a + b;');
console.log(add(2, 3));
// Use a named function
function add(a, b) {
return a + b;
}
console.log(add(2, 3));
// Or use an anonymous function
const add = function(a, b) {
return a + b;
};
console.log(add(2, 3));
Avoid Code Serialization in JavaScript
Code serialization involves taking JavaScript code and turning it into a string. This can be risky if user inputs are directly converted into executable code. Avoid code serialization to prevent unintentional code execution.
Example:
Avoiding Code Serialization: Be cautious when converting user inputs to code. Instead, use predefined functions or manipulate data without turning it into executable code:
// Avoid code serialization
const userInput = "console.log('This could be dangerous');";
const code = JSON.parse(userInput);
// Use predefined functions
function displayMessage(message) {
console.log(message);
}
displayMessage('This is safe.');
// Manipulate data without executing code
const userInput = "console.log('This could be dangerous');";
const sanitizedInput = userInput.replace(/console\.log/g, '');
console.log(sanitizedInput); // Output: 'This could be dangerous'Use Code Analysis Tools
Use a Node.js Security Linter
Node.js security linters are specialized tools that help identify potential security vulnerabilities, code quality issues, and adherence to best practices in your Node.js applications. These linters can analyze your codebase and provide feedback on potential security threats and areas for improvement.
How to Use a Node.js Security Linter:
- Choose a Node.js Security Linter: There are several security linters available for Node.js, such as ESLint with security plugins, like ESLint-plugin-security, or specialized security linters like snyk, nsp, or eslint-plugin-security.
- Install and Configure: Install the selected linter as a development dependency in your Node.js project. Configure the linter to include security-specific rules and plugins.
- Run Regular Scans: Integrate the linter into your development workflow. Run it regularly as part of your continuous integration pipeline and during code reviews.
Use a Static Code Analysis (SCA) Tool
As discussed earlier, Static Code Analysis (SCA) tools are designed to analyze source code without executing it. They identify a wide range of issues, including security vulnerabilities, code style violations, and potential bugs. These tools are highly valuable for maintaining code quality and preventing code injection vulnerabilities.
Security Systems and Measures
Implement Intrusion Detection Systems (IDS)
Intrusion Detection Systems (IDS) are critical components of your security infrastructure. They are designed to monitor network traffic and system activities for signs of unauthorized access, attacks, or policy violations. IDS can be network-based or host-based, and they play a vital role in early threat detection.
How to Implement IDS:
- Choose the Right Type: Select the type of IDS that suits your network and application architecture. Network-based IDS (NIDS) analyzes network traffic, while host-based IDS (HIDS) focuses on individual hosts.
- Deployment: Deploy IDS sensors strategically within your network, ensuring they have visibility into key traffic flows and systems.
- Configuration and Tuning: Fine-tune your IDS to reduce false positives and maximize detection accuracy. Customize the rules and alerts based on your application’s behavior and potential threats.
- Incident Response: Develop an incident response plan to react swiftly to IDS alerts. An IDS should be part of a broader security strategy that includes threat analysis and response protocols.
External Security Measures, i.e., WAF (Web Application Firewall)
A Web Application Firewall (WAF) is a security system designed to protect web applications from a variety of threats, including code injection attacks, by monitoring and filtering HTTP requests. It acts as a barrier between the application and potential attackers.
Community Engagement and Reviews
Bug Bounty Programs
Bug bounty programs are initiatives that invite security researchers, ethical hackers, and the broader cybersecurity community to discover and responsibly disclose vulnerabilities in your applications. Engaging in bug bounty programs helps you identify and fix security issues before malicious actors exploit them.
How to Set Up a Bug Bounty Program:
- Clearly define the scope of your bug bounty program, specifying which assets, applications, and services are eligible for testing.
- Establish clear rules of engagement, including reporting procedures, expected conduct, and compensation guidelines for researchers.
- Use established bug bounty platforms like HackerOne or Bugcrowd to launch and manage your program. These platforms provide a structured environment for interaction between researchers and your team.
- Maintain open and transparent communication with researchers and acknowledge their contributions. Timely responses and payments are key to a successful program.
- Regularly assess and refine your program based on feedback and evolving threats. Encourage researchers to focus on specific areas of concern.
Engage with the Security Community
Engaging with the broader security community is essential for staying informed about emerging threats and best practices. It can also provide valuable insights into potential vulnerabilities in your applications.
How to Engage with the Security Community to Prevent Code Injection:
- Attend security conferences and events, such as BlackHat, DEFCON, and OWASP AppSec, to learn about the latest trends and network with security professionals.
- Participate in security-related online forums, mailing lists, and communities. Platforms like Reddit’s r/netsec and the OWASP mailing list are valuable sources of information.
- Collaborate with security researchers, both internally and externally, to identify and address vulnerabilities. Encourage responsible disclosure.
- Follow reputable security blogs and podcasts to stay updated on security news, trends, and best practices.
- Engage in threat intelligence sharing programs and platforms to receive and provide information about emerging threats and vulnerabilities.
Code Injection Remediation
If a code injection attack is detected, it is important to take immediate action to remediate the attack and mitigate the damage. The following steps should be taken to remediate a code injection attack:
- Identify the source of the attack. This can be done by reviewing the application logs and by using network analysis tools.
- Isolate the affected systems. This will prevent the attacker from spreading the attack to other systems.
- Patch the vulnerability. This will prevent the attacker from exploiting the vulnerability again.
- Change all passwords. This will prevent the attacker from using compromised passwords to access other systems.
- Notify affected users. This will allow users to take steps to protect their accounts.
Conclusion
Code injection attacks are a serious security threat to your system’s integrity, data privacy, and overall security and can have devastating consequences for websites and web applications. We’ve highlighted critical measures to prevent code injection attacks, from validating and sanitizing user inputs to employing allowlists, avoiding client-side validation, and much more. By following these practices, you can fortify your code against vulnerabilities that malicious code injections can exploit.
Additionally, code injection attacks can potentially extend to other vulnerabilities like command injection attacks. In a command injection attack, the attacker’s primary goal is to execute malicious commands through the application. This often involves manipulating user input or other data to include a malicious system command. If the application doesn’t adequately validate and sanitize the inputs and instead directly processes them as commands, it can execute operating system commands with potentially harmful consequences.
Remember, security is not a one-time effort; it’s an ongoing commitment. Regular code reviews, engagement with the security community, and active participation in bug bounty programs will continuously reinforce your defenses.



How to Prevent Code Injection Attacks: From Detection to Prevention